Admin
Admin
.jpg)
מספר הודעות : 138
Join date : 05.06.09
 |  נושא: Event Viewer נושא: Event Viewer  Mon 26 Dec 2011, 20:12 Mon 26 Dec 2011, 20:12 | |
|  סקירה על Event Viewer הכוללת סרטונים והסבר מפורט עם תמונות על Event Forwarding סקירה על Event Viewer הכוללת סרטונים והסבר מפורט עם תמונות על Event Forwarding סרטון מצוין של איל מלח: הסבר על הפיצ'רים ב Event Viewer לצפיה במסך מלא יש להקיש לחיצה כפולה באמצעות העכבר.
Event Viewer is a tool used to monitor the health of the computer. Event Viewer has had a significant overhaul in Windows Vista and is now closely integrated with Task Scheduler and the Reliability and Performance Monitor. You can access Event Viewer in Administrative Tools and use it to perform the following functions:
View and filter events from a multitude of preconfigured logs.
Create and save custom event filters and views.
Configure tasks to run in response to specified events.
Configure and manage event subscriptions.
The preconfigured logs fall into two categories—Windows Logs and Applications and Services Logs—as shown in Figure 3.26.

Figure 3.26 The main window in Event Viewer shows the Windows Logs and Applications and Services Logs.
As you expand Applications and Services Logs > Microsoft > Windows, you discover dozens of additional, preconfigured event logs. These logs address specific services and features of the operating system and can be used to identify problems, before they start, as well as provide diagnostic and troubleshooting information after something unexpected has happened.
There are two more collections of logs available within Event Viewer:
Analytic Logs—Describe program operations and indicate problems that cannot be addressed with human intervention. Analytic logs generate a high volume of output.
Debug Logs—Used to help developers troubleshoot issues with their programs.
Exam Alert
These two logs are hidden by default due to their specialized nature and large volume of output. You can make them visible and functional by enabling them from the View > Show Analytic and Debug Logs menu item, as shown in Figure 3.27.

Figure 3.27 Showing the Analytic and Debug Logs in Event Viewer.
Event Forwarding
Event Forwarding is used to consolidate events from multiple computers, called Source computers, onto a single monitoring station, called the Collector computer. Event types include all the event categories in the Windows Logs and Applications and Services Logs. Both Source and Collector computers must be specially configured for Event Forwarding to be successful.
TIP
To configure Event Forwarding, you should log on to the Source and Collector computers using a domain administrator user account.
Source Computer Configuration
On the Source computers, you must configure the Windows Remote Management utility by executing the following command at an elevated privilege command prompt:
winrm quickconfig
This command makes some changes to your system, including setting the WinRM service to auto start; creates a WinRM Listener on HTTP to accept Web Services for Management (WS-Man) requests—a mini, nonuser-configurable web server); and opens the firewall for WinRM services.
You must also add the computer account of the Collector computer to the local Administrators group on each Source computer.
NOTE
Finding Computers You must enable the adding of computer accounts to the local Administrators group on each Source computer by selecting Object Type > Computers in the Select Users, Computers or Groups dialog box in the local Administrators group properties.
Collector Computer Configuration
On the Collector computer, you must configure the Windows Event Collector Utility by executing the following command at an elevated privilege command prompt:
wecutil qc
This command initializes the Windows Event Collector on the Collector computer. Now you are ready to create subscriptions on the Collector computer to Source computer events.
NOTE
Required Services The Windows Remote Management (WinRM) service and the Windows Event Collector Service must be started on the Source and Collector computers. By default, these services are set to start up manually. You should configure them for automatic startup to ensure proper functionality and future use of their services.
Exam Alert
Here's a quick review:
You must configure the Windows Remote Management utility by running winrm on the Source computers.
You must configure the Windows Event Collector Utility by running wecutil on the Collector computer.
You should familiarize yourself with the basic functions of these two commands by running the executables followed by the /? switch.
To configure subscriptions, in Event Viewer on the Collector computer, right-click Subscriptions in the left pane and select Create Subscription. The Subscriptions Properties page is shown in Figure 3.28.

Figure 3.28 Configuring an event subscription on the Collector computer.
NOTE
First Things First Subscriptions can be established only with properly configured Source computers.
By clicking Select Events, you see that events can be largely unfiltered to acquire large amounts of data or finely filtered to acquire only a very specific and smaller number of events. The Query Filter dialog box for the Subscription is shown in Figure 3.29.
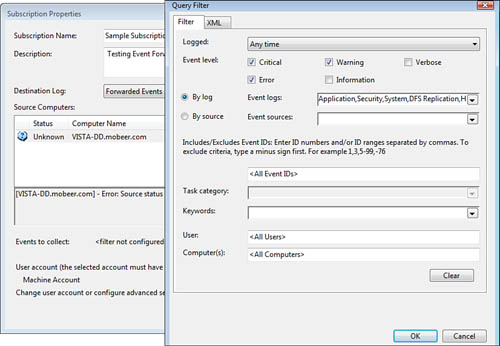
Figure 3.29 Configuring a Query Filter to limit the types of events collected on the Collector computer.
The Advanced button on the Subscription Properties dialog box allows for the configuration of the account that will read the log files. This account must have permissions to access the log files and is the typically the computer account that you placed in the local Administrators group on the Source computers. You can also configure the forwarded event delivery for Bandwidth or Latency optimizations.
Exam Alert
Also on the Advanced Subscription Settings dialog box, you can configure events to be forwarded using the HTTP protocol over port 80 (the default), or they can be transmitted securely using HTTPS, which is the HTTP protocol over a Secure Sockets Layer (SSL) tunnel. The HTTPS protocol runs over port 443 and requires a computer certificate to authenticate the Source computer to the Collector computer and to establish the encrypted SSL tunnel. Any firewalls between Source computers and the Collector computer require the appropriate port (80 or 443) to be opened. The User Account, Event Delivery Optimization, and transmission Protocol configuration settings are shown in Figure 3.30.

Figure 3.30 Advanced Subscription Settings provides access to the User Account, Event Delivery Optimization, and transmission Protocol configuration settings
| |
|



